
EC-
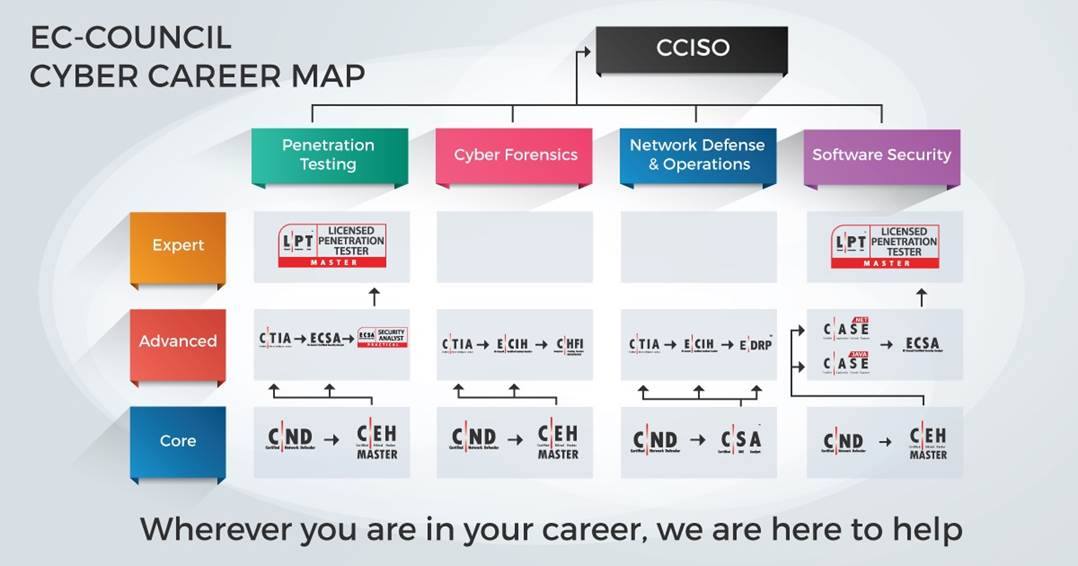
EC-Council Partnership
e.KRAAL has partnered with EC-Council as an authorized reseller of top notch cybersecurity courses, EC-Council is the world’s largest cyber security technical certification body.
EC-Council has trained more than 80,000 people, certifying over 30,000 cyber security specialists from organizations such as Microsoft, IBM, the United Nations, the FBI and the US Army.
EC-COUNCIL BROCHUREEc-Council Courses
Certified Ethical Hacker (CEH)

Certified Ethical Hacker (CEH)
The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training program that any information security professional will need.This course will immerse you into a 'Hacker Mindset' in order to teach you how to think like a hacker and better defend against future attacks. It puts you in the driver’ s seat with a hands - on training environment employing a systematic ethical hacking process.
Certified Chief Information Security Officer (CCISO)

Certified Chief Information Security Officer (CCISO)
The Certified CISO (CCISO) program is aimed at producing top-level information security executives. The CCISO does not focus solely on technical knowledge but on the application of information security management principles from an executive management point of view.
Certified Application Security Engineer (CASE JAVA/CASE .NET)

Certified Application Security Engineer (CASE JAVA/CASE .NET)
Focuses on secure application software development processes. It is a, hands-on, comprehensive application security course that will help you create a secure application software. This course encompasses security activities involved in all phases of the Secure Software Development Lifecycle (SDLC): Planning, creating, testing, and deploying an application.
Certified Incident Handler V2 (ECIH V2)

Certified Incident Handler V2 (ECIH V2)
Designed to provide the fundamental skills to handle and respond to computer security incidents in an information system. Provides incident response training by addressing various underlying principles and techniques for detecting and responding to current and emerging computer security threats. After attending the course, you will be able to create incident handling and response policies and deal with various types of computer security incidents.
Certified Secure Computer User (CSCU)

Certified Secure Computer User (CSCU)
This course is specifically designed for todays’ computer users who use the internet extensively. The purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets.
Certified Encryption Specialist (ECES)

Certified Encryption Specialist (ECES)
The program introduces professionals to the field of cryptography. Participants will learn the foundations of modern symmetric and key cryptography including the details of algorithms such as Feistel Networks, DES, and AES. Anyone involved in the selection and implementation of VPN’s or digital certificates should attend this course.
Advanced Penetration Tester (APT)

Advanced Penetration Tester (APT)
This course prepares you for the LPT (Master) certification exam and covers the testing of modern infrastructures, operating systems and application environments. It also covers the process to document and prepare a professional penetration testing report.
Certified Threat Intelligence Analyst (CTIA)

Certified Threat Intelligence Analyst (CTIA)
This is a combination of cyber security and threat intelligence to help identify and mitigate business risks by converting unknown internal and external threats into known threats. It is a comprehensive, specialist-level program that teaches a structured approach for building effective threat intelligence.
Computer Hacking Forensic Investigator (CHFI)

Computer Hacking Forensic Investigator (CHFI)
This course covers knowledge of digital forensic techniques and standard forensic tools to collect the intruder’s footprints necessary for his investigation. It delivers on methodological ways to deal with digital forensics, including seizing, chain of custody, acquisition preservation, analysis and presentation of digital evidence.
Certified Security Analyst/Licensed Pentester (ECSA)

Certified Security Analyst/Licensed Pentester (ECSA)
The ECSA course is a fully hands-on program with labs and exercises that cover real world scenarios. By practicing the skills that are provided to you in the ECSA class, we are able to bring you up to speed with the skills to uncover the security threats that organizations are vulnerable to.
Certified Network Defender (CND)

Certified Network Defender (CND)
This course prepares Network Administrators on network security technologies and operations to attain Defence-in-Depth network security skills. It contains hands-on labs, based on major network security tools and techniques which will provide Network Administrators real world expertise on current network security technologies and operations.
EC-Council Disaster Recovery Program (EDRP)

EC-Council Disaster Recovery Program (EDRP)
EDRP provides the professionals with a strong understanding of business continuity and disaster recovery principles, including conducting business impact analysis, assessing of risks, developing policies and procedures, and implementing a plan. It also teaches professionals how to secure data by putting policies and procedures in place, and how to recover and restore their organization’s critical data in the aftermath of a disaster.
Ethical Hacking Core Skills (EHCS)

Ethical Hacking Core Skills (EHCS)
This course is the first step on the EC Council Pen testing career track. In this course you will learn the core skills to build a solid : ecurity foundation.
Licensed Penetration Tester (LPT)

Licensed Penetration Tester (LPT)
The LPT (Master) standardizes the knowledge base for penetration testing professionals by incorporating best practices followed by experienced experts in the field. The objective is to ensure that each licensed professional follows a strict code of ethics, is exposed to the best practices in the domain of penetration testing and aware of all the compliance requirements required by the industry
Certified Ethical Hacker (CEH) (Practical)

Certified Ethical Hacker (CEH) (Practical)
C|EH Practical is a six-hour, rigorous exam that requires you to demonstrate the application of ethical hacking techniques such as threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking, web app hacking, etc. to solve a security audit challenge.
Certified Security Analyst/Licensed Pentester (ECSA) (Practical)

Certified Security Analyst/Licensed Pentester (ECSA) (Practical)
ECSA (Practical) is a 12-hour, rigorous practical exam built to test your penetration testing skills.
Certified Blockchain Professional

Certified Blockchain Professional
CBP digs deep into the main characteristics and features of the distributed ledger technology as well as intorduces Blockchain's new 3S (Secure,-Scalable-Sustainable) proprietary framework.
Certified SOC Analyst (SOC)

Certified SOC Analyst (SOC)
CSA is the first step to joining a security operation center(SOC). It is enginereed for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entry-level and intermediate-level operations.
Ec-Council Workshops
Risk Management Approach & Practices Workshop

Risk Management Approach & Practices Workshop
The risk management course is specifically designed to guide a CISO in defining and implementing a risk management approach within an IS program.
Dark Web Forensics Deep Dive Workshop

Dark Web Forensics Deep Dive Workshop
This is an in-depth workshop on Dark web Forensics investigations including technical details of how the dark web/TOR works and a tour of actual dark web markets.
Malware & Memory Deep Dive Workshop

Malware & Memory Deep Dive Workshop
This course assumes basic understanding of PC'S, networks and basic forensics. The purpose is to teach students essential memory forensics.
Mobile Forensics Deep Dive Workshop

Mobile Forensics Deep Dive Workshop
This is a two day course designed to immerse person in phone forensics.
Get in Touch
Contact us on Course Enrollment
